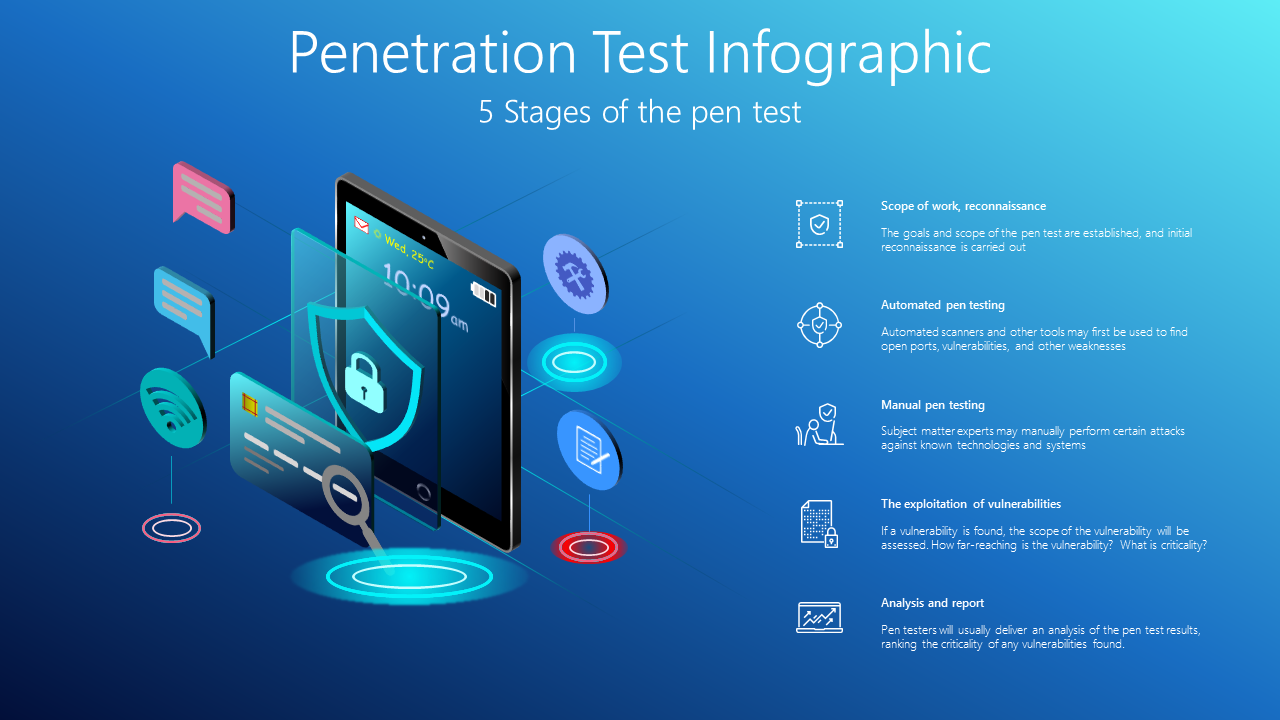
? Wed, 25oC, 10:09am, Scope of work, reconnaissance, The goals and scope of the pen test are established, and initial reconnaissance is carried out, Automated pen testing, Automated scanners and other tools may first be used to find open ports, vulnerabilities, and other weaknesses, Manual pen testing, Subject matter experts may manually perform certain attacks against known technologies and systems, The exploitation of vulnerabilities, If a vulnerability is found, the scope of the vulnerability will be assessed. How far-reaching is the vulnerability? What is criticality?, Analysis and report, Pen testers will usually deliver an analysis of the pen test results, ranking the criticality of any vulnerabilities found.
Only logged in customers who have purchased this product may leave a review.
You may also like…
Infographics Packs
Mega Deals
RELATED INFOGRAPHICS COLLECTIONS
Technology AI Blockchain Infographics
Infographics Collections
Technology AI Blockchain Infographics
Technology AI Blockchain Infographics


































Reviews
There are no reviews yet.